之前开启全站SSL,用的是虚拟主机DA面板自带的一键功能,后来老失败,改用的FreeSSL现在又要手机号,考虑到有多台服务器,决定手动申请通配符证书,以后到期重新申请一次就行,不用再担心碰到一些乱七八糟的事情。
但过程远没那么简单,坑永远都在。。。
安装Certbot
按官方的指导文件安装即可,我家庭服务器用的Ubuntu 20.04 LTS,接下来的命令都是在这台机器上运行的。
参考官方文档的好处是,有些文章的内容已经过期了,比如有些使用certbot-auto这个工具的文章
- Windows: https://certbot.eff.org/lets-encrypt/windows-other
- Ubuntu: https://certbot.eff.org/lets-encrypt/ubuntufocal-other
使用Certbot的手动模式向Let’s Encrypt 申请证书
- 先上手动模式的用户手册:https://certbot.eff.org/docs/using.html#manual
- Certbot帮助文档命令: Cerbot -h All , 该命令会显示所有子命令和选项的说明
我所使用的命令如下:
sudo certbot certonly --manual --preferred-challenges=dns-01certonly 是子命令,只申请或续约证书,不安装。让你可以在任意一台联网的PC设备上申请证书,不必是你的服务器
–manual 选项指以交互或Shell脚本的方式提交信息,我没有脚本,默认是交互方式
–preferred-challenges 选项以指定域名认证方式,http-01是文件认证,dns-01是DNS解析指定TXT认证,这里用的DNS认证,文件认证没试过,毕竟我的目标是脱离服务器来申请证书
一般还会加一个选项 –server https://acme-staging-v02.api.letsencrypt.org/directory 用以指定Let’s Encrypt 服务器目录,但如果你仔细看过Certbot的帮助文档,你会发现默认的就是这个服务器,这里可以省略
提交信息
运行上面的命令后,则进入交互模式,以提交相关信息,先是邮箱
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator manual, Installer None
Enter email address (used for urgent renewal and security notices)
(Enter 'c' to cancel): 然后是必定要同意的协议
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server. Do you agree?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: 再然后是一些新闻之类的邮件推送,可以不接受
Would you be willing, once your first certificate is successfully issued, to
share your email address with the Electronic Frontier Foundation, a founding
partner of the Let's Encrypt project and the non-profit organization that
develops Certbot? We'd like to send you email about our work encrypting the web,
EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: N输入域名,通配符域名不包含主域名,所以要填上两个,用逗号分隔
Account registered.
Please enter in your domain name(s) (comma and/or space separated) (Enter 'c' to cancel): yywr.net,*.yywr.net通过DNS认证域所有权
接下来会给出需要做DNS TXT记录验证的信息,这里需要注意,这里会出现两次Press Enter to Continue,每一次都给出一串TXT验证字符, 出现第二次的时候一定要等DNS生效再按回车键
Requesting a certificate for yywr.net and *.yywr.net
Performing the following challenges:
dns-01 challenge for yywr.net
dns-01 challenge for yywr.net
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please deploy a DNS TXT record under the name
_acme-challenge.yywr.net with the following value:
D7jxyoXXXXXXXXXXXXXXXXXXXXXXXXXXXGdncSBDU
Before continuing, verify the record is deployed.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please deploy a DNS TXT record under the name
_acme-challenge.yywr.net with the following value:
I8GXXXXXXXXXXXXXXXXXXXXXXXXXXXXc4Y2Z-11lk
Before continuing, verify the record is deployed.
(This must be set up in addition to the previous challenges; do not remove,
replace, or undo the previous challenge tasks yet. Note that you might be
asked to create multiple distinct TXT records with the same name. This is
permitted by DNS standards.)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to ContinueDNS解析设置
接下来就是我被坑的部分了,个人对DNS解析相关的知识有限,不知道是不是因年纪大了,我看到提示后的理解是添加两个名称为_acme-challenge.yywr.net 的TXT记录,值记录分别使用提供的字符串就好,结果一直验证不过
后来想到是不是不需要后面的域名,而这时刚好看到另一篇文章提到的主机名称为_acme-challenge,改完后很快就能找到记录了
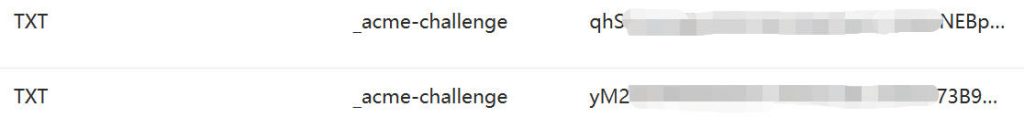
可以使用下面命令查看DNS解析是否生效,查询的时候就需要名称+域名了
- Linux:
dig -t txt _acme-challenge.yywr.net - Windows:
nslookup -q=txt _acme-challenge.yywr.net
解析生效会返回ANSWER信息,未生效的话则没有,踩坑的时候以为是时间不够没生效,愣了睡了个觉起来再试,注意解析记录不要删除
dig -t TXT _acme-challenge.yywr.net
; <<>> DiG 9.16.1-Ubuntu <<>> -t TXT _acme-challenge.yywr.net
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 60200
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;_acme-challenge.yywr.net. IN TXT
;; ANSWER SECTION:
_acme-challenge.yywr.net. 3600 IN TXT "D7jxyoXXXXXXXXXXXXXXXXXXXXXXXXXXXGdncSBDU"
_acme-challenge.yywr.net. 3600 IN TXT "I8GXXXXXXXXXXXXXXXXXXXXXXXXXXXXc4Y2Z-11lk"
;; Query time: 200 msec
;; SERVER: fe80::1%2#53(fe80::1%2%2)
;; WHEN: Sun Apr 11 13:48:11 CST 2021
;; MSG SIZE rcvd: 154获取证书
在确认DNS解析生效之后即可以按回车继续提交,失败会有红色文字提示,一般就是DNS解析未成功,成功则返回类似下面的信息
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/yywr.net/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/yywr.net/privkey.pem
Your certificate will expire on 2021-07-10. To obtain a new or
tweaked version of this certificate in the future, simply run
certbot again. To non-interactively renew *all* of your
certificates, run "certbot renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le可以从提示中看到,证书密钥相关都保存在 /etc/letsencrypt/live/yywr.net/这个目录下,部署到服务器就好,我用的宝塔和Directadmin面板,直接贴证书内容就好,其它的还没弄过,就不展开说了。
关于续期
运行命令再来一次即可,完成之后就会发现证书已经延期了,不需要再次部署。
或者用 root 身份,使用 Crontab 加个定时任务 0 0 */60 * * root certbot renew --quiet --renew-hook "service nginx reload"
参考文章:
- https://blog.csdn.net/u012291393/article/details/78768547
- https://jingsam.github.io/2018/10/12/lets-encrypt.html